New Tech Forum provides a venue for technology leaders—including vendors and other outside contributors—to explore and discuss emerging enterprise technology in unprecedented depth and breadth.
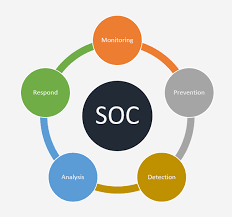
A Security Operations Center (SOC) specializes in monitoring and analyzing data to detect cyber threats and prevent attacks from them. They work to sort actual

According to Aberdeen Group and Ventana Research, one out of four enterprises surveyed expect their data to grow by more than 30 percent in the

In today’s rapidly, and continually, evolving data landscape, maintaining the sovereignty and security of sensitive data is paramount. With data privacy and security becoming an

In collaboration with Microsoft and NVIDIA, we’ve integrated NVIDIA NIM microservices and NVIDIA AgentIQ toolkit into Azure AI Foundry—unlocking unprecedented efficiency, performance, and cost optimization

Every year on March 14 (3.14), AWS Pi Day highlights AWS innovations that help you manage and work with your data. What started in 2021

Data Privacy , Data Security , Government ‘Dogequest’ Site Provided Tesla Owners Addresses, Names and Phone Numbers Chris Riotta (@chrisriotta) • March 19, 2025
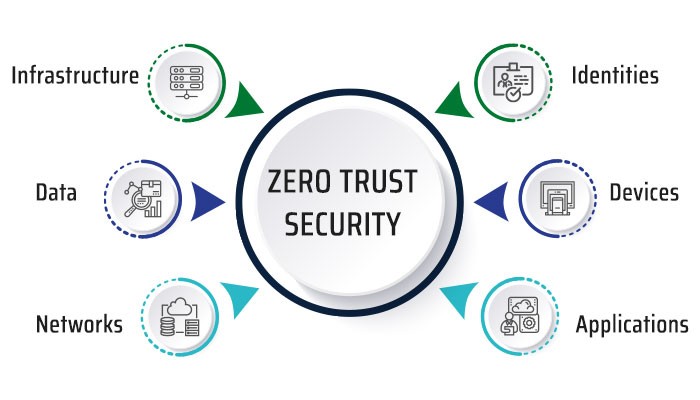
Zero trust security takes an “never trust, always verify” approach to access control. Access is only granted once an individual’s identity and context have been

Timepopo – shutterstock.com Experten des Sicherheits-Unternehmens Trend Micro haben eine als ZDI-CAN-25373 bezeichnete Sicherheitslücke in Windows entdeckt, die Angreifer seit mindestens 2017 ausnutzen. Über die Lücke können die
Kerberos is a protocol for authenticating service requests between trusted hosts across an untrusted network, such as the internet. By providing a gateway between users
