Critical Infrastructure Security , Encryption & Key Management , Security Operations Cyber Agency Urges Critical Infrastructure Operators to Migrate Within the Deadline Akshaya Asokan (asokan_akshaya)
Category: Updates

Cyber threats can wreak havoc on businesses, from data breaches to loss of reputation. Luckily, there are effective strategies available that can reduce cybersecurity risk.

Angreifer nutzen die zunehmende Verbreitung von und das Vertrauen in Captcha-Überprüfungen aus, um Malware zu verbreiten. Sie leiten Opfer auf manipulierte Websites und fordern sie
A pass-the-hash attack is an exploit in which an attacker steals a hashed user credential and — without cracking it — reuses it to trick
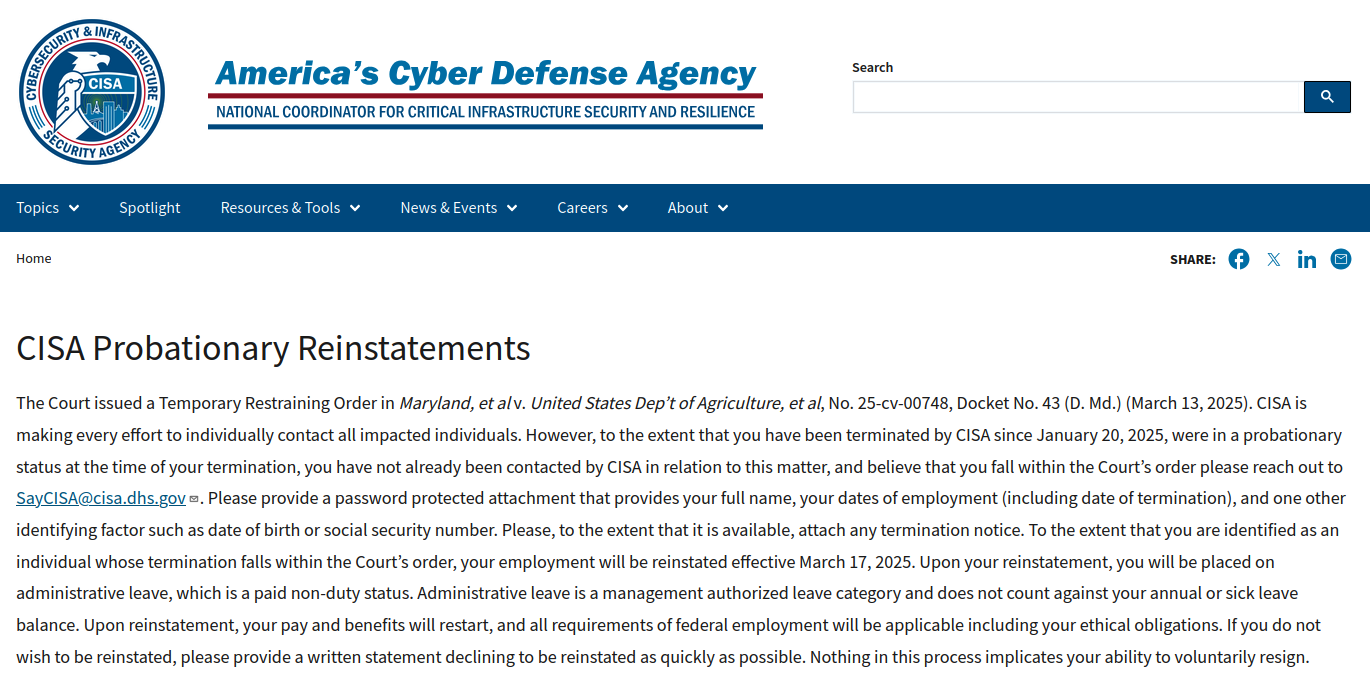
A message posted on Monday to the homepage of the U.S. Cybersecurity & Infrastructure Security Agency (CISA) is the latest exhibit in the Trump administration’s

Bengaluru, India, March 19th, 2025, CyberNewsWire Moving Beyond Detection to Real-Time, Automated Security Across Workloads, Cloud, and Infrastructure SecPod, a global cybersecurity provider, has announced
A buffer overflow occurs when a program or process attempts to write more data to a fixed-length block of memory, or buffer, than the buffer

A new Windows zero-day vulnerability is being actively exploited by at least 11 hacking groups linked to nation-states including North Korea, Iran, Russia, and China

Microsoft on Tuesday released 57 patches affecting 10 product families. Six of the addressed issues are considered by Microsoft to be of Critical severity, and

Cryptocurrency isn’t just a buzzword anymore. By December 2024, the number of global cryptocurrency owners reached approximately 659 million, marking a 13% increase from January
